
Risk Identification
15 March 2019Table of Contents
Risk Identification
The next planning effort in risk management after risk planning is risk identification. The purpose of this process is to identify all potential risks in the project regardless of their probability or their impact. Assessment will be done later in a following process.
Identification is being done using various techniques such as information gathering techniques, documents review, checklist analysis, assumption analysis, and SWOT analysis.
The output of this process is a table contains all identified potential risks with initial information concerning every item of them. This table is known as risk register. Through the following clauses, we are going to discuss these techniques and the risk register.
1 – Information Gathering Analysis
Examples of data gathering techniques are brainstorming, Delphi technique, interviewing, root cause analysis, and mind mapping. Figure-1 shows an example of mind mapping
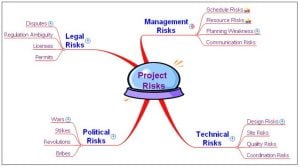
Figure-1 : Mind Mapping for Potential Project Risks
2- Documentation Review
One of the most effective methods to identify a significant number of potential risks is to review project documents. This method allows you to explore and discover most areas of project activities starting from the very early milestones of project initiation passing with all the phases, decisions, evaluations, and studies of the project. These documentation includes project charter, project management plan and its subsidiary plans, WBS, time schedule, activity duration estimates, activity cost estimates, stakeholder register, contracts, and procurement documents. The following chart is a hierarchy of potential project documents.
3 – Checklist Analysis
This checklist is a list contains predefined risks that you can check them if they are potential in your project. It can be developed based on historical information from past projects. The lowest level of RBS can be used as a checklist as in Figure-2. It’s very quick to use it and you will have a lot of risks identified. However, it should not be the only tool that is being used for this purpose. The reason behind this advice is that usually there are risks that are not listed in this checklist. Hence if you only depend on this checklist, other risks will be neglected.
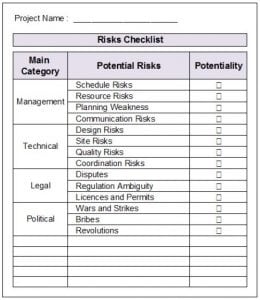
Figure2 : Risks Checklist
4- SWOT Analysis
SWOT analysis is a famous technique that is being used to identify and evaluate the strength and weakness in the project and organization in order to find out expected opportunities and threats. Table-1 shows an example of SWOT analysis.
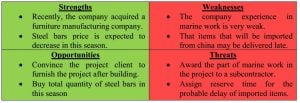
Table-1: SWOT Analysis
5 – Risk Register
Risk register is an ouput of all risk management processes that come after risk planning. It’s a dynamic database that contains all the identified risks and is being filled with the information regarding these risks such as description, category, propability, impact, planned response, assigned person for action, risk status, retained reserve for this risk, …etc
Through the process of identify risks, this table is being filled with risks in addition to the root cause and initial proposed response. Table-2 shows an example of risk register till this point.
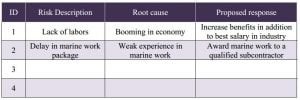
Table-2 : Risk Register (Initial View)


